
The recent leak of personal and banking details of up to 400,000 individuals and companies was likely a “hacker’s cache” that was being collated to plan another attack, a cybersecurity expert has said.
Earlier this week, hundreds of thousands of documents uploaded to a popular file-sharing site. The data included mobile phone numbers, details of international bank transactions, online passwords and credit cards numbers, many from Qatar National Bank (QNB) customers.
QNB has said it is investigating the breach, but has not updated customers about the matter since Tuesday.
Curiously, many of the files also contained details about individuals’ social media accounts and photographs of their friends and relatives.
Simon Edwards, a cybersecurity architect at IT security company Trend Micro, told Doha News today that many of these files could have been part of the hacker’s own research, and had nothing to do with QNB.
“It is not the bank doing any of this; more that this is like a cache of the hackers ‘loot’ (which) I don’t think was ever meant to see the light of day.
It is more like the data file got out as they were trying to exfiltrate it, much like a burglar might drop a stolen TV on his escape,” he said.
Writing about the hack on Trend Micro’s blog site yesterday, Edwards said that an initial inspection of the documents suggests the hacker “breached bank data to build up profiles on specific individuals in order to launch follow-on attacks.”
In addition to showing the actual information, the leaked files also reveal how the hacker got his data, Edwards said.
The inclusion of folders on particular groups of individuals, such as Al Jazeera staff and defense and intelligence personnel, suggests the hacker’s motives could be more political than financial, he added.
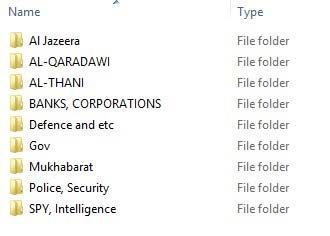
“There is a large amount of data surrounding transactional information on the bank’s customers, detailing payments moving in and out of accounts. … These almost exclusively point to foreign financial transactions, in the most part paid to accounts in Jordan,” Edwards said in his post.
“As the transactional data is worked through, will we find a connection between those being profiled and the highlighted financial transactions?”
He added that while it is troubling for those whose details have been made public, such hacks are not that unusual.
“This is happening all over the world, and all the time,” he said.
Social media attacks
It is important to know that all the information we post on social media accounts can be used by hackers as part of a bigger target – often corporations or large organizations.
“We all share too much information on ourselves, which hackers can use to build profiles, which they can then use to target cyber attacks. Here, (the QNB hack) we have a good example of it being done,” Edwards told Doha News.
Hackers who want to break into an organization typically profile people who work there, usually through social media accounts such as LinkedIn and Facebook.

An attacker may find the account of a person who works at the targeted firm, and send them a friend request. Even if that person doesn’t accept it, the hacker can also see their friends, and send them requests.
If one of them accepts, the hacker can then get access to his initial target’s Facebook account, for example, and can see what clubs they may belong to.
They can then launch a phishing attack, sending an email to the target pretending to be the admin of a club, asking to complete a document.
The document is infected with malware, which, if opened on a work computer, can infect the machine and download a trojan – which then allows the attacker to have access to the target’s computer.
In many cases, this may give the hacker wider access to the company’s network.
Advice
To limit exposure to such attacks, experts suggest taking standard “common sense” precautions such as ensuring lots of personal details are not revealed online by checking security settings.
They also advise exercising caution before letting people into personal networks.
This would entail checking them out before accepting their invitations, installing up-to-date malware protection for all devices and being cautious about opening files sent over the internet, which could be part of a phishing attack.
On the corporate side of things, Edwards suggested restricting access to sensitive data to as few people as possible; requiring two-step verification for login; and install sophisticated software to detect and stop attacks.
Thoughts?







